Most code security programs are still built around the idea that you can “catch up” on application risk with periodic full-repo reviews and a steady diet of traditional SAST alerts.
That time has passed.
A survey of software professionals found that most respondents said their organizations have more than 100 times the volume of code they had 10 years ago. This was before vibe coding transformed our workflows. Add that explosion of code into the mix, and that gap gets wider. AI has accelerated the era of “Big Code” and it’s outpacing security coverage.
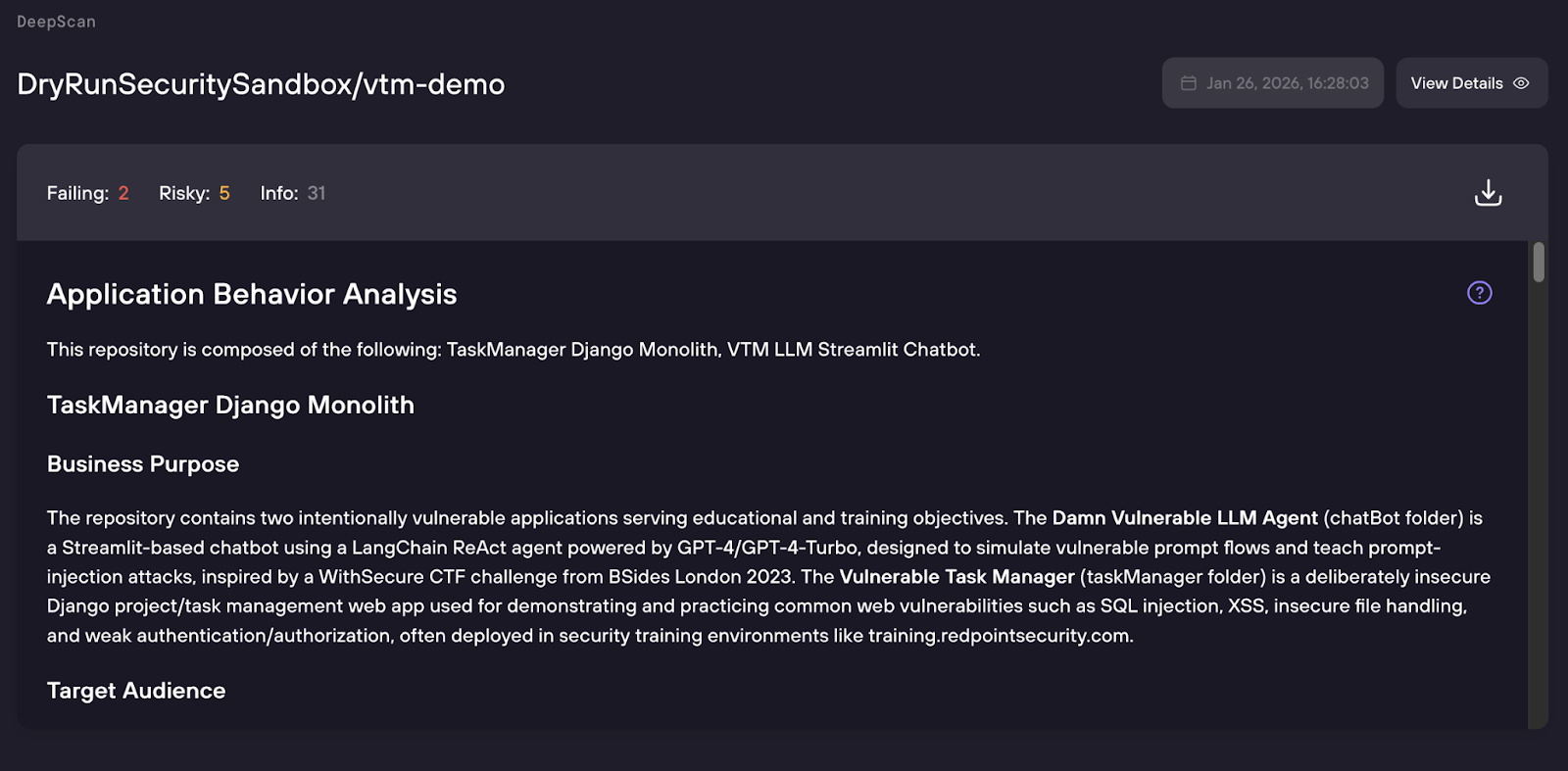
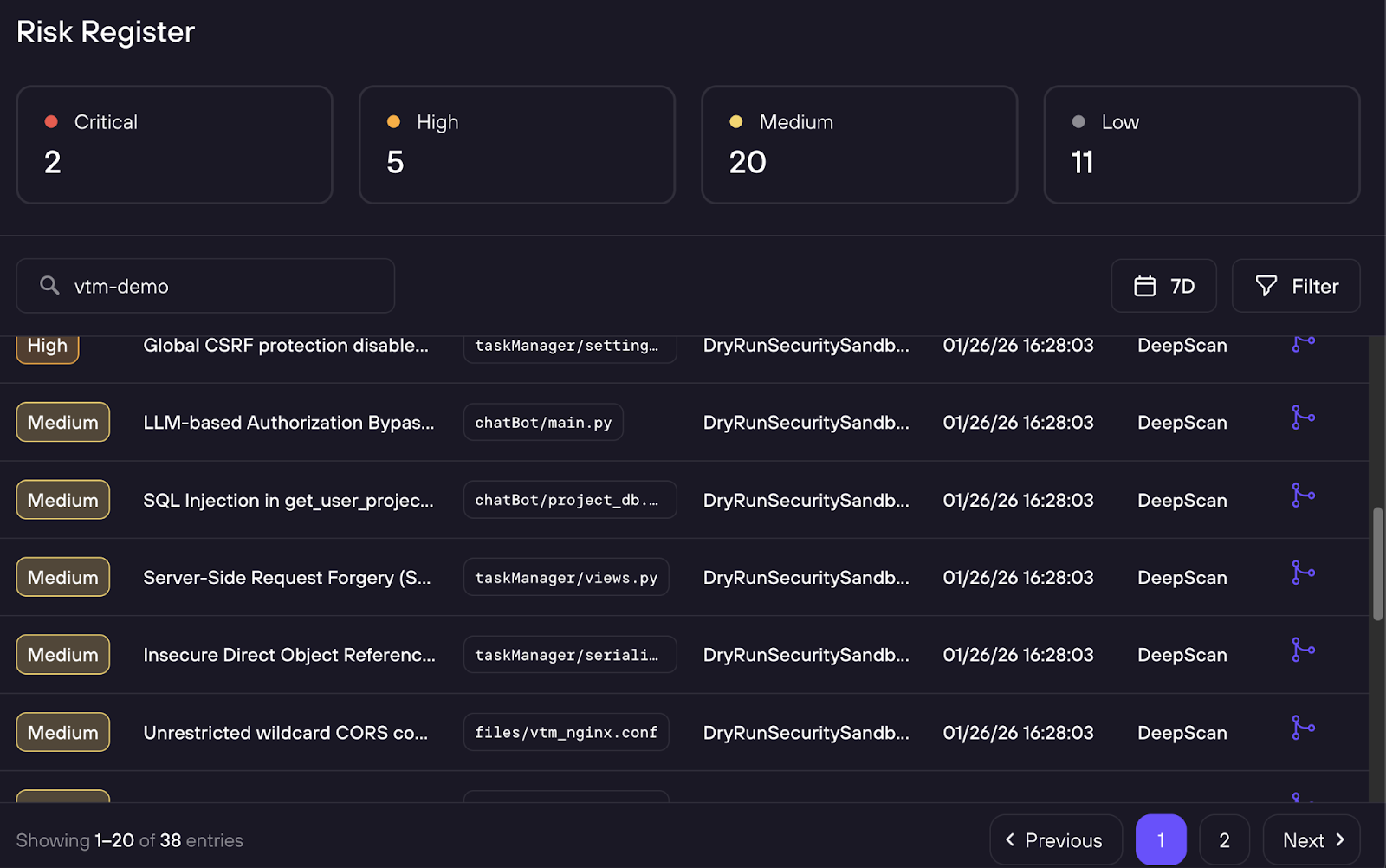
To address this challenge, today we’re announcing the DryRun Security DeepScan Agent. It expands our code security intelligence from individual pull requests to all the code in your repos. Like a senior security engineer, it produces a report of prioritized, high-signal security findings by reasoning about your code. It replaces weeks of manual source code review with an on-demand assessment in about an hour, so AppSec and Product Security teams can reduce false positives and focus on issues that carry real impact.
DeepScan assessment segment
DeepScan risk segment, rolled up into unified risk for for security leaders
Before today, a full security review usually meant hiring a consultant or pulling an internal expert off roadmap work for 2 to 4 weeks. They run scanners and dependency checks, then spend time filtering out nonsense, talking with devs, learning the app’s patterns, and manually hunting for the issues automation cannot see. The report is valuable, but it takes time, costs a lot, and still consumes engineering time to sort signal from noise.
Now, you can get the human reviewer outcome (and more), on demand. Run the DeepScan Agent in your repo and you’re securing code in a few hours. It filters out junk findings automatically and produces a focused report with the risks that actually move the needle. It also closes the gap where scanners fall short by reasoning about the code like a reviewer would, surfacing difficult logic and access-control flaws, secrets, and business logic risks. The team gets actionable results fast, spends less time triaging, and can run a full-repo assessment whenever the code changes, not just when budget and schedules allow.
This is code security intelligence expanded to full secure code reviews.
How DeepScan Agent is different from traditional SAST
Traditional SAST is syntax-first. It answers, “Does this pattern appear?”
DeepScan Agent is intent-first. It answers, “What does this code do, how can it fail, and what is the risk if it fails?”
In practice, that means:
- Full-repo context. Many serious issues are only found when you trace identity, data flow, and trust boundaries across the codebase. DeepScan builds that map, then uses it to assess exploitability the way an experienced reviewer would.
- Signal over noise. DeepScan delivers a honed set of findings that matter, not thousands of low-value alerts.
- Human-grade prioritization. Findings are risk-ranked with clear impact, plus remediation guidance engineers can use without translation.
What DeepScan Agent finds that scanners miss
DeepScan Agent surfaces classes of vulnerabilities that traditional tooling struggles to reason about, including multi-tenant isolation bypasses, complex IDORs, authorization logic that breaks across specific workflows, business logic flaws, and secrets exposure that gets lost in a sea of noise.
These are the failures that lead to data exposure, customer impact, and serious compliance and reputational damage.
We have had a core group of customers testing DeepScan for months, and we’re seeing that even mature security programs with robust tooling and processes still uncover high-impact flaws when they run DeepScan Agent across a full repo. They are often dormant bugs missed by legacy tooling. They are the issues that require understanding how the application actually behaves end to end. DeepScan Agent does not find more issues. It finds the ones that mattered all along.
What you get in a DeepScan report
DeepScan Agent produces output you can use immediately: a prioritized set of findings, clear explanations grounded in your application context, and actionable remediation steps. The goal is simple: less time triaging, more time fixing.
How DeepScan strengthens pull request security
A full repo security scan should not be a one-off artifact. The context DeepScan builds becomes a multiplier for pull request security. When DryRun Security understands and collects how your system is structured and where trust boundaries sit, the composition of the application, and everything else a security reviewer would need - PR analysis gains new depth. This is true code intelligence where architectural patterns, business context, data classification, and other security-relevant information morphs into contextual security analysis that evaluates change risk inside the real application, before issues ship.
When to run DeepScan Agent
DeepScan Agent is useful any time you need full-repo confidence quickly: before major releases, after significant refactors, during acquisitions, or other major milestones. Additionally, the same contextual data that deepscan captures and is used to improve our PR agent also enables our Insights agent to become the most robust inventory and asset management tools in application security today. It is just another way we leverage code intelligence. When you need audit evidence or when leadership asks “Are we exposed to X?” you will have a full, accurate, polished report for them in minutes. Think about the recent Shai Hulud attacks. It took our team minutes to decipher whether or not we were at risk. If you can’t say the same thing about your App/Prod-Sec program, you should come check us out!
A turning point for application security
We are entering a phase where automation can behave like an expert reviewer, at machine speed. However, DeepScan Agent does not replace humans. It amplifies expertise, eliminates wasted effort, and closes the gap between what scanners can detect and what experts know actually cause breaches.
Availability
DeepScan Agent is available today to DryRun Security customers and trial users. If you want to see DeepScan Agent on one of your repositories, request a DryRun Security demo.